Resource Sanitization»
The Terraform state can contain very sensitive data. Sometimes this is unavoidable because of the design of certain Terraform providers or because the definition of what is sensitive isn't always simple and may vary between individuals and organizations.
Spacelift provides two different approaches for sanitizing values when resources are stored or passed to Plan policies:
- Default Sanitization: All string values are sanitized.
- Smart Sanitization: Only the values marked as sensitive are sanitized.
For example, if we take the following definition for an AWS RDS instance:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 | |
Spacelift will supply something similar to the following to any plan policies:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 | |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 | |
As you can see in the example above, with the Default Sanitization all string values are hashed which makes it difficult to comprehend logs, work with outputs/created resources, and write policies against the changes in your stacks. With Smart Sanitization, only sensitive values are hashed.
Smart Sanitization allows you to author Plan policies against non-sensitive string values without the need for a call to the sanitized() function.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 | |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 | |
Info
The same sanitization is also applied to resources shown in the resources views.
Default Sanitization»
Unless you enable Smart Sanitization, or disable Sanitization altogether, Default Sanitization will be used.
Smart Sanitization»
Info
Due to limitations in the data output by Terraform, Smart Sanitization can only be used on stacks that use Terraform versions 1.0.1 or above. Using an unsupported version will fail.
As we rely on the sensitive argument in Terraform to determine which of your values are sensitive we recommend that you ensure your variables, outputs, and resources have their sensitive arguments set properly.
How to enable Smart Sanitization in your stacks»
When using the Spacelift User Interface»
If you're using the Spacelift user interface to create your stacks, you can enable Smart Sanitization in your existing stack settings page under the "Vendor" section. If you're creating new stacks it will be an option when you select your Terraform version in our wizard.
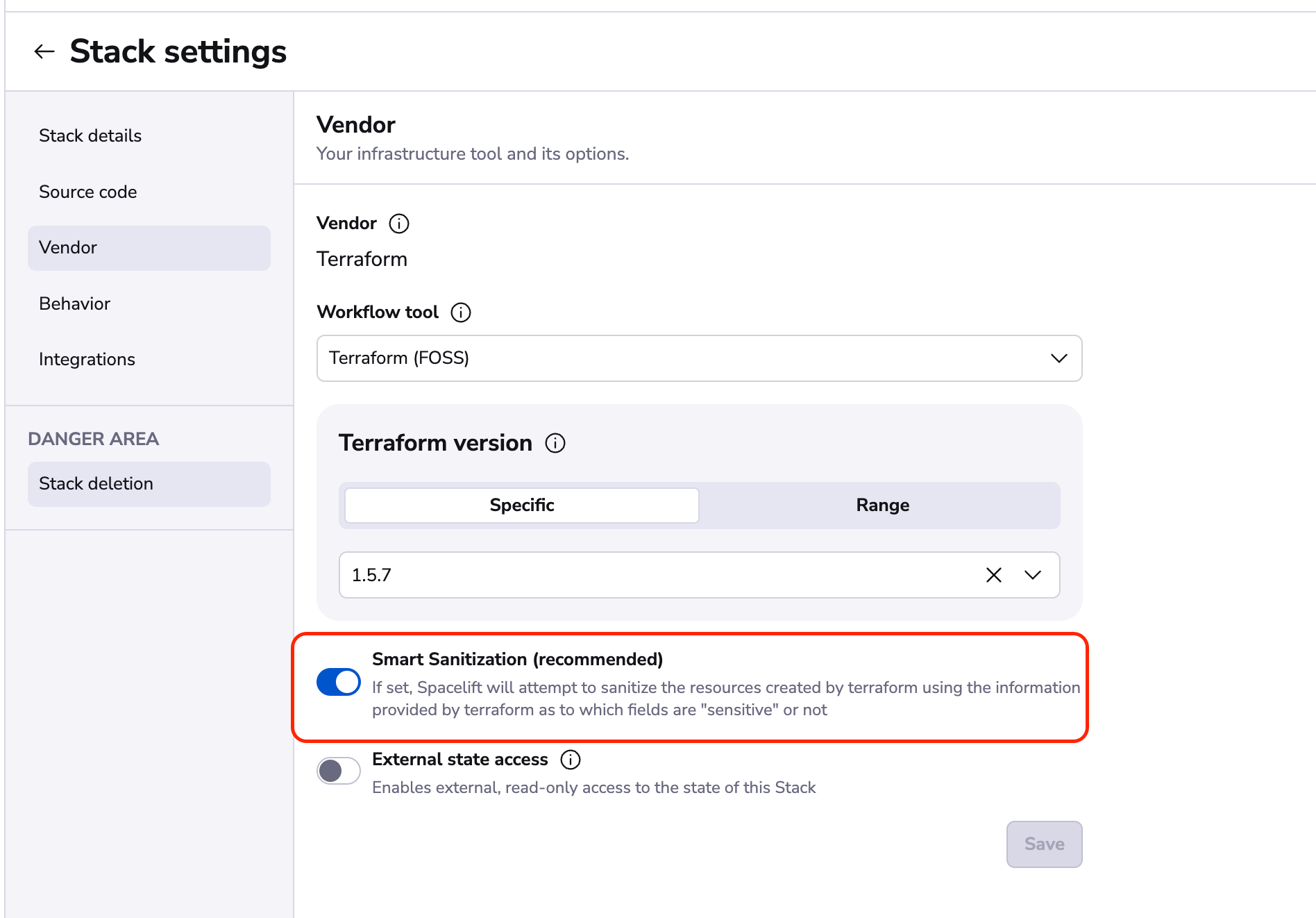
When creating stacks with the Spacelift Terraform Provider»
If you’re using the Spacelift Terraform provider for creating Spacelift stacks, you are able to set the property terraform_smart_sanitization. For example, to create a simple stack you can use the following code:
1 2 3 4 5 6 7 8 9 | |
Disabling Sanitization»
If you have a situation where the sanitized() helper function doesn't provide you with enough flexibility to create a particular policy, you can disable sanitization completely for a stack. To do this, add the feature:disable_resource_sanitization label to your stack. This will disable sanitization for any future runs.