Audit trail»
Info
This feature is only available to Enterprise plan. Please check out our pricing page for more information.
Spacelift supports auditing all operations that change Spacelift resources. We provide a built-in audit log as well as webhook functionality to allow you to optionally store your audit logs in a third party system.
Built-in logs»
As an admin, you can view Audit trail logs by navigating to the Audit trail section of your account settings and choosing the logs tab:
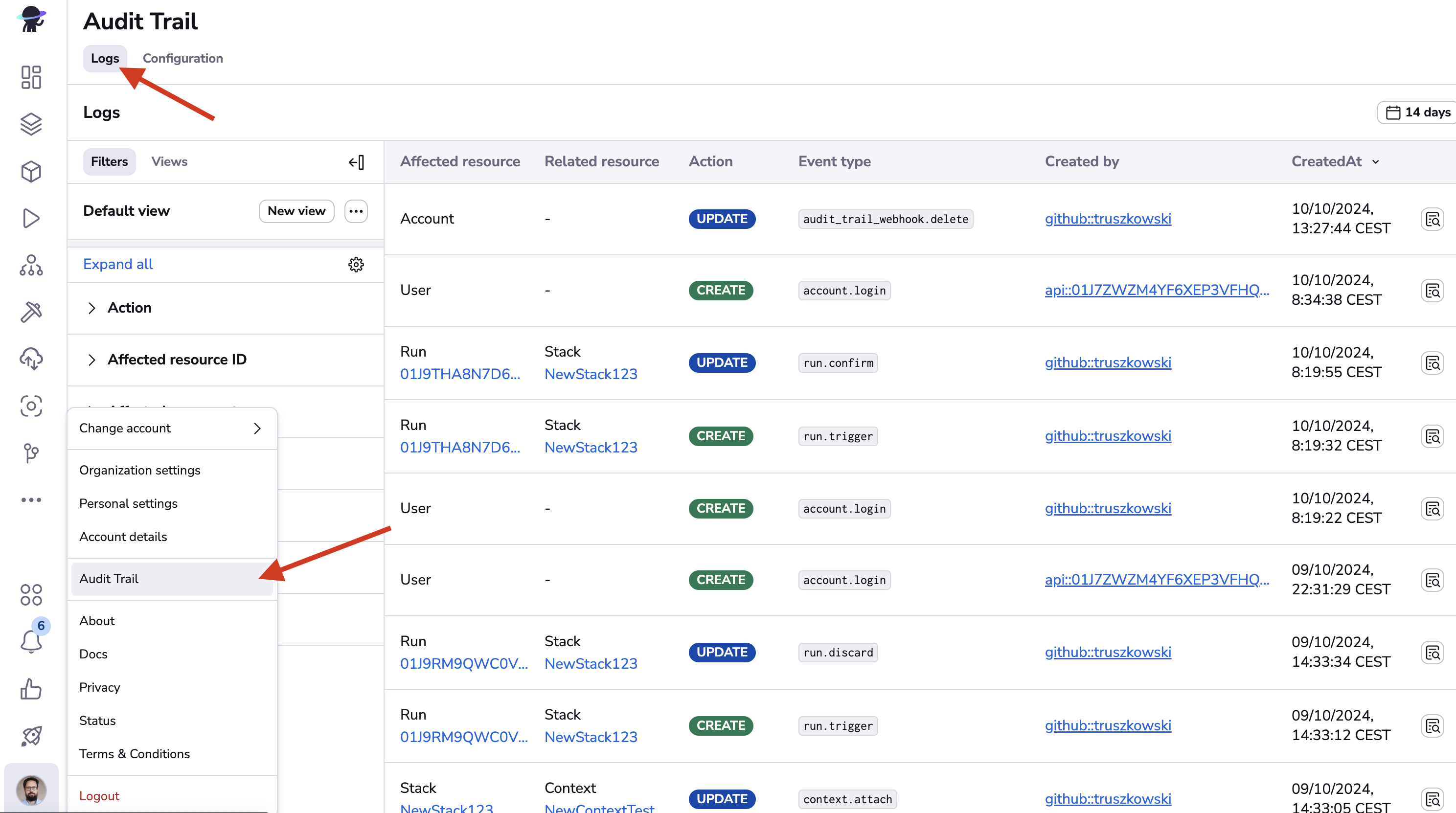
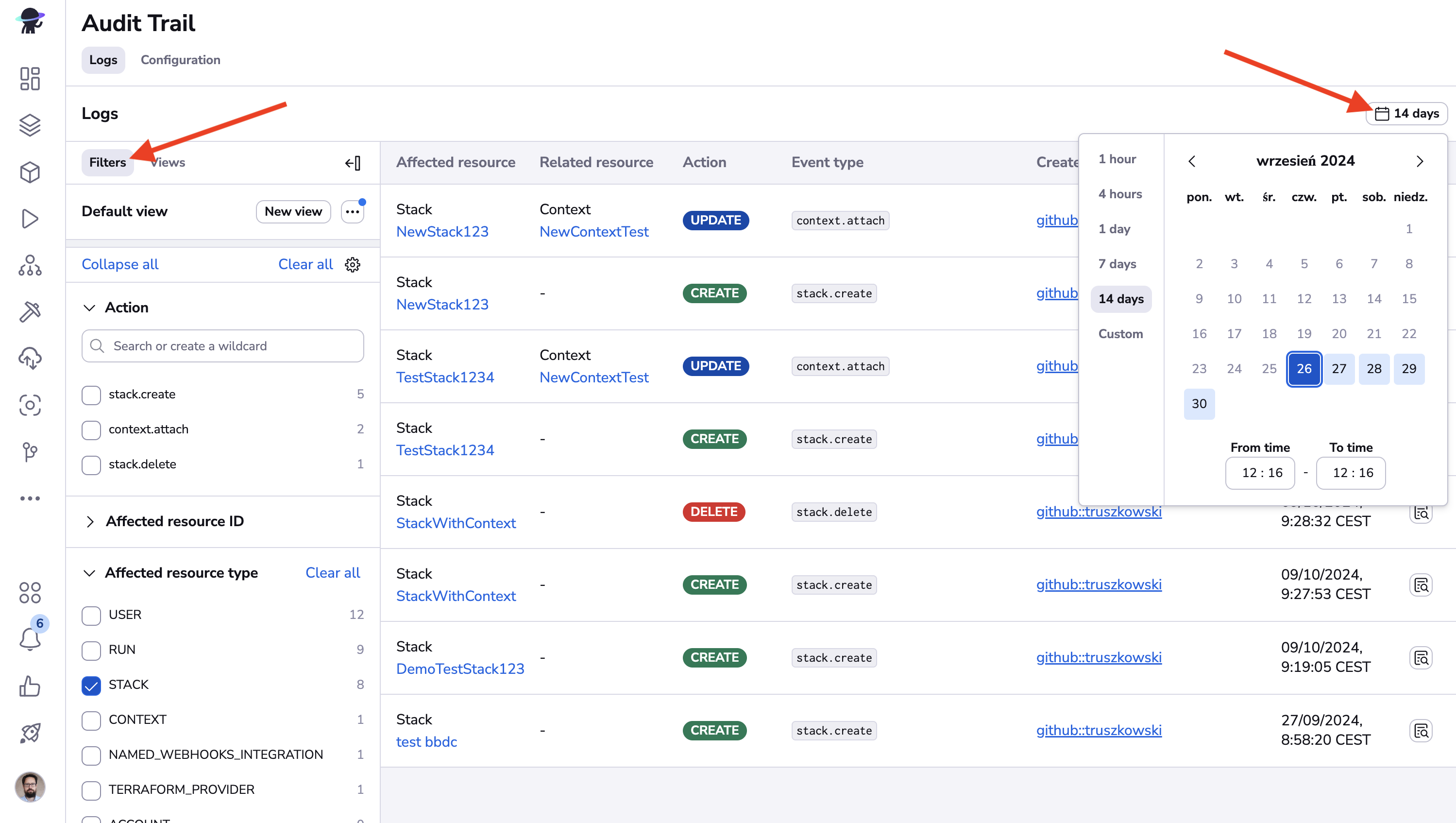
You can look for specific events using filters (on the left side) and the date picker (in the top-right corner).
You can see the details:
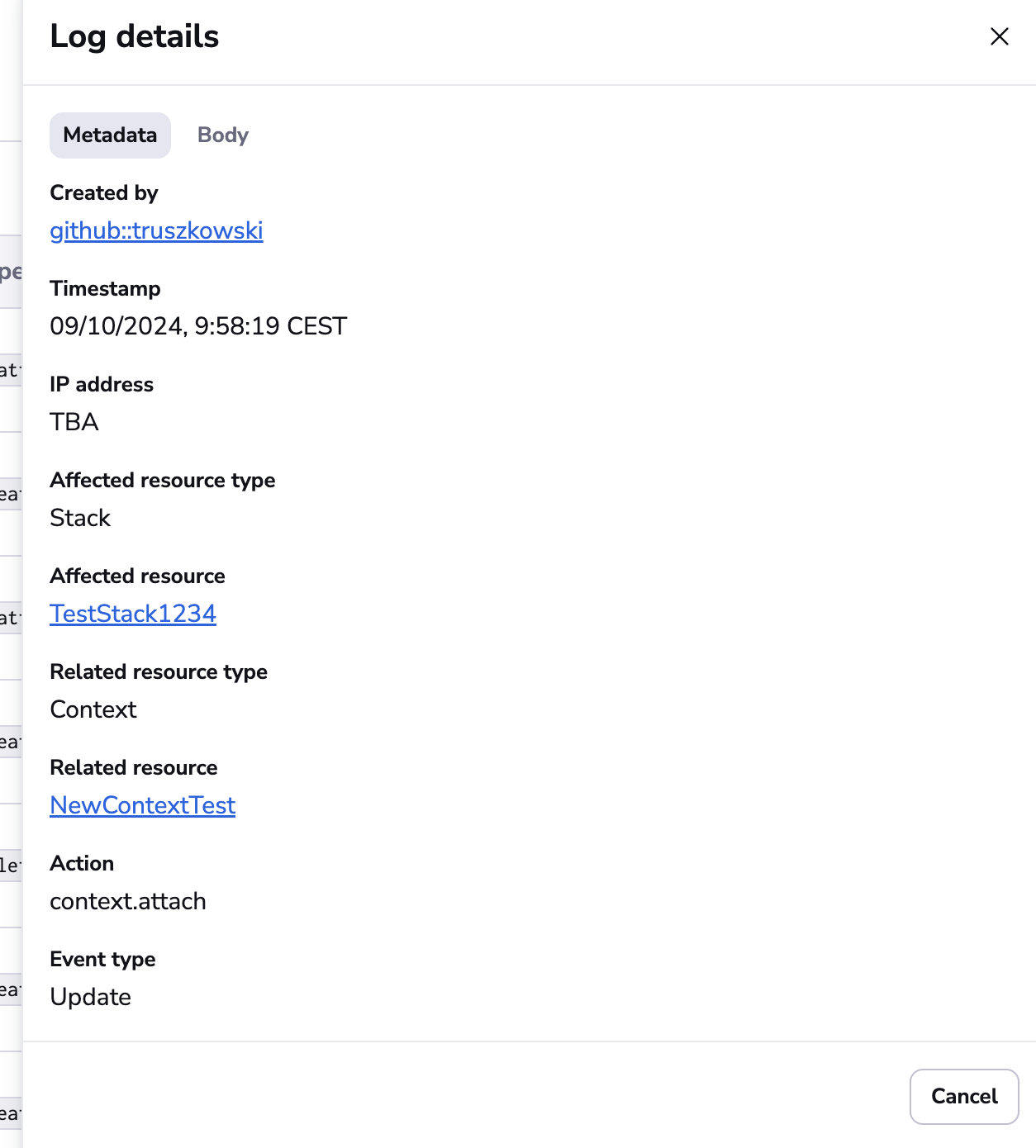
You can also go to the affected resource or apply another filter:
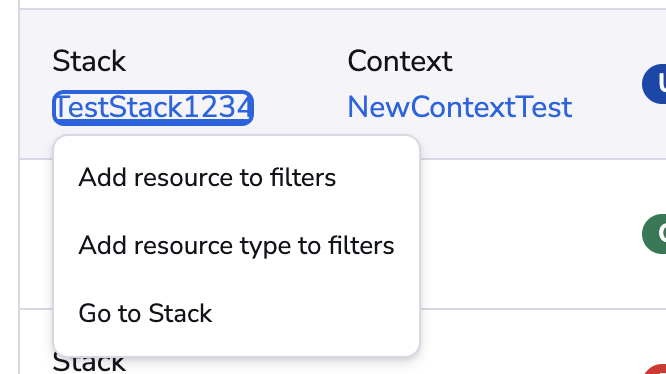
Retention»
Logs are kept for 30 days.
Webhook Setup»
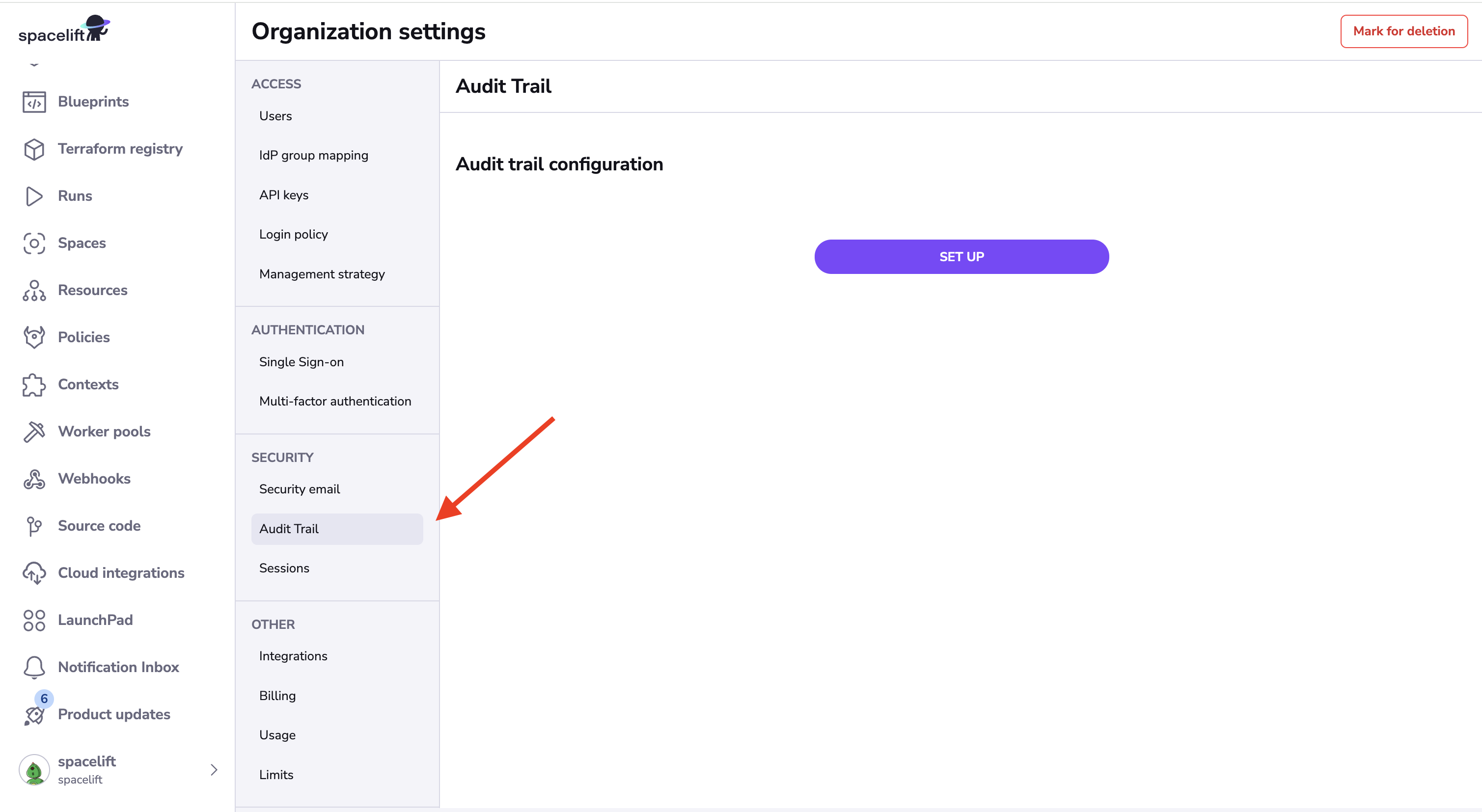
In order to set up webhooks for audit events, navigate to the Audit trail section of your account settings and choosing the configuration tab, and click the Set up button:
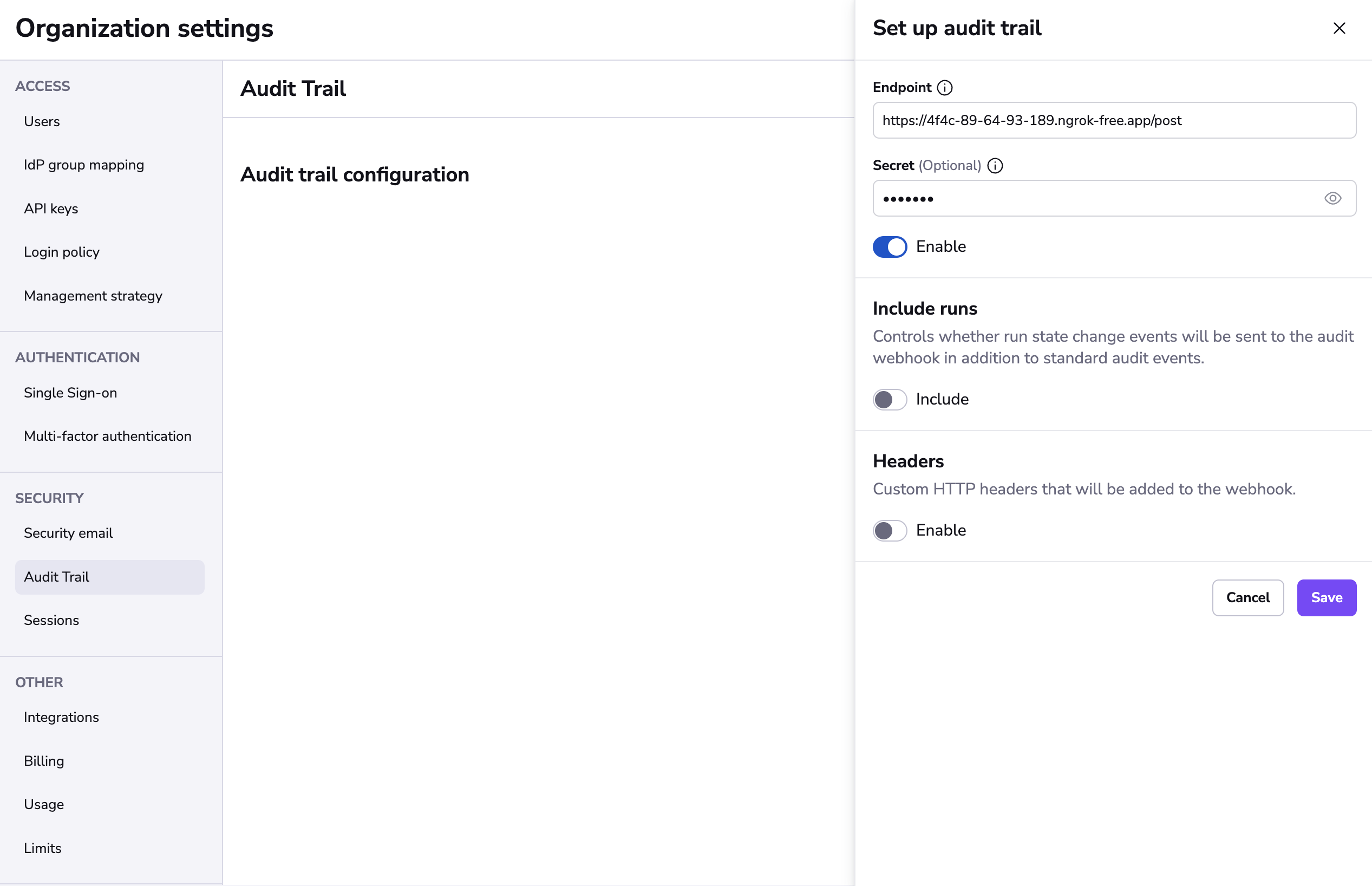
You will then need to provide a webhook endpoint and an arbitrary secret that you can later use for verifying payload.
Optionally you can specify the custom headers that will be added to each HTTP request and enable Include runs option, which controls whether run state change events will be sent to the audit webhook in addition to standard audit events.
Let's use ngrok for the purpose of this tutorial:
If you choose to automatically enable the functionality, clicking the Save button will verify that payloads can be delivered (the endpoint returns a 2xx status code). This gives us an opportunity to look at the payload:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 | |
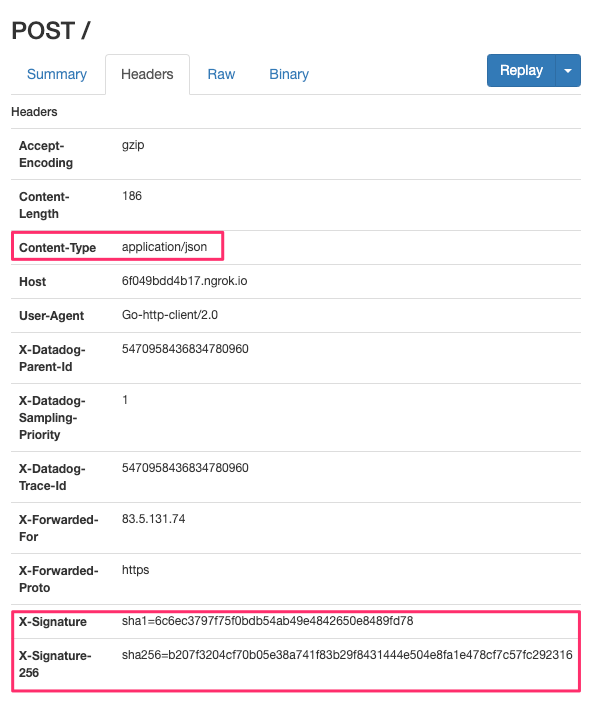
...and the headers - the interesting ones are highlighted:
Usage»
Every audit trail payload conforms to the same schema:
account: name (subdomain) of the affected Spacelift account;action: name of the performed action;actor: actor performing the action - the::format shows both the actor identity (second element), and the source of the identity (first element)actor_roles: (optional) array of role slugs attached to the actor when the action was performed. Only present when the actor has role attachments (e.g., stacks with role bindings);context: some contextual metadata about the request;data: action-specific payload showing arguments passed to the request. Any sensitive arguments (like secrets) are sanitized;
Below is a sample:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 | |
Disabling and deleting the audit trail»
The audit trail can be disabled and deleted at any point, but for both events we will send the appropriate payload. We suggest that you always treat these at least as important security signals, if not alerting conditions:
1 2 3 4 5 6 7 8 9 10 11 12 | |
Verifying payload»
Spacelift uses the same similar verification mechanism as GitHub. With each payload we send 2 headers, X-Signature and X-Signature-256. X-Signature header contains the SHA1 hash of the payload, while X-Signature-256 contains the SHA256 hash. We're using the exact same mechanism as GitHub to generate signatures, please refer to this article for details.
Sending logs to AWS»
We provide a reference implementation for sending the Audit Trail logs to an AWS S3 bucket.
It works as-is but can also be tweaked to route the logs to other destinations with minimal effort.
Failures»
Audit trail deliveries are retried on failure.