Stack»
If you're managing your infrastructure in Spacelift, you're managing them with stacks. A stack is a combination of source code, the current state of the managed infrastructure (e.g. OpenTofu/Terraform state file) and the configuration (environment variables and mounted files). A stack is also an isolated, independent entity.
Unless you're only using Spacelift to host and test private OpenTofu/Terraform modules, your account should contain one or more stacks.
What can I do with stacks?»
- Create, delete, and lock stacks.
- Organize stacks.
- Configure stack settings.
- Schedule stack runs.
- Set up stack dependencies.
- Detect drift in managed stacks.
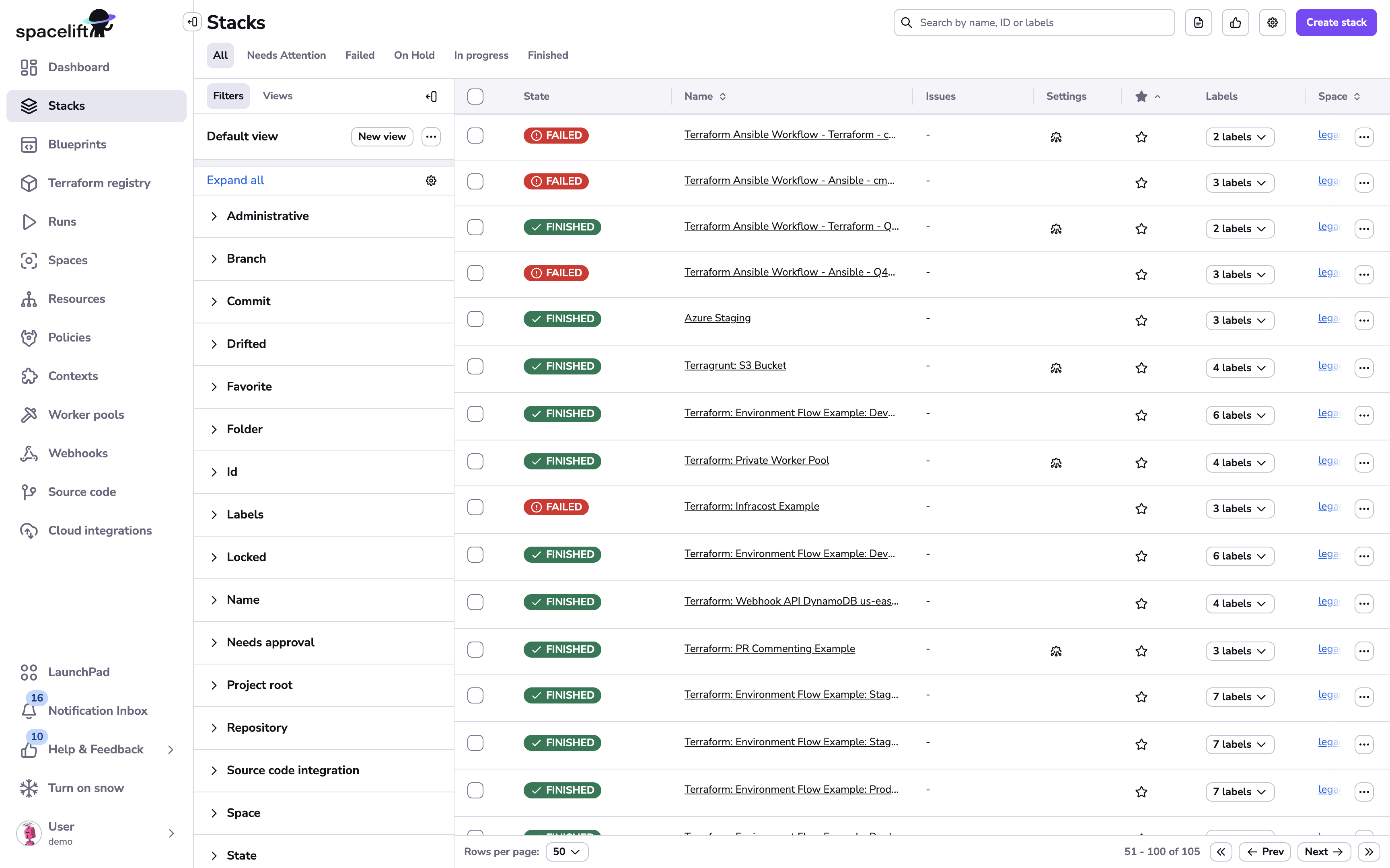
Stack state»
Similar to runs and tasks, stacks also have states that are generally equal to their most recent tracked run state.
The state is set to "None" on stacks with no runs:

Stack states show users the overall health of their infrastructure, and the level of development activity associated with it, at a glance.