Google Cloud Platform (GCP)»
Info
We strongly recommend using OIDC for the GCP integration.
Spacelift's GCP integration allows Spacelift to manage your Google Cloud resources without the need for long-lived static credentials by creating a service account inside the project dedicated to your Stack. We show you the globally unique email of this service account, which you can add to your GCP organizations and/or projects with the right level of access.
With the service account already created, Spacelift generates temporary OAuth token for the service account as a GOOGLE_OAUTH_ACCESS_TOKEN variable in the environment of your runs and tasks. This is one of the configuration options for the Google Terraform provider, so you can define it like this:
1 | |
Many GCP resources require the project identifier too, so if you don't specify a default in your provider, you will need to pass it to each individual resource that requires it.
Integrate GCP in the Spacelift UI»
OAuth Scopes»
You can customize the list of OAuth scopes that the token is granted when it's generated. When you're setting up your GCP integration through the web UI, we suggest the following list of scopes:
https://www.googleapis.com/auth/computehttps://www.googleapis.com/auth/cloud-platformhttps://www.googleapis.com/auth/ndev.clouddns.readwritehttps://www.googleapis.com/auth/devstorage.full_controlhttps://www.googleapis.com/auth/userinfo.email
This list is consistent with the defaults requested by the Terraform provider.
Set up integration»
To set up the GCP integration in Spacelift, you must already have a stack configured.
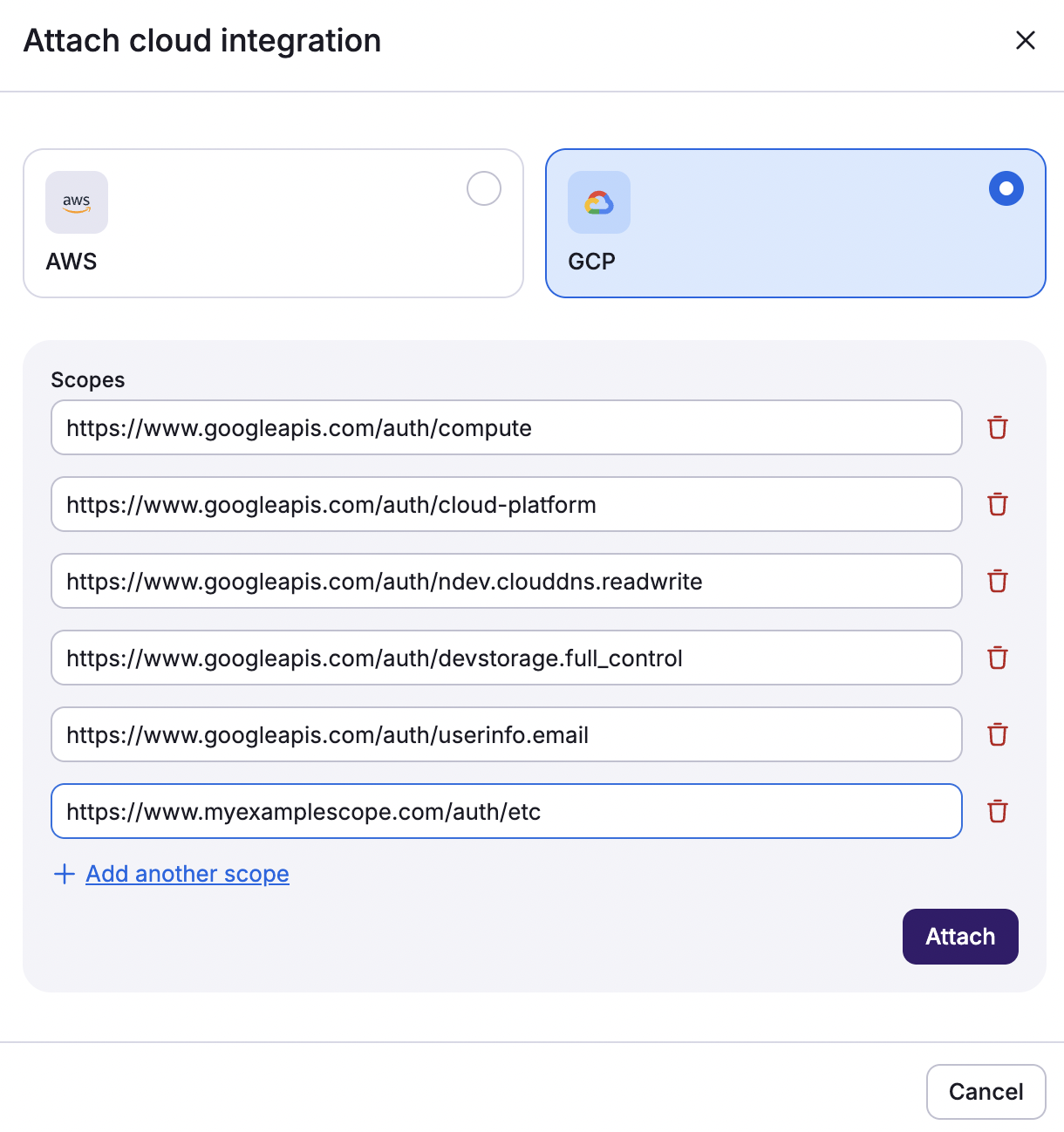
- On the Ship Infra > Stacks tab, click the three dots beside the stack you would like to integrate with GCP.
- Click Settings, then click Integrations.
- Click Attach cloud integration.
- Select GCP, then verify the OAuth scopes.
- If you need to add additional scopes, click Add another scope, then type in the scope.
- Click Attach.
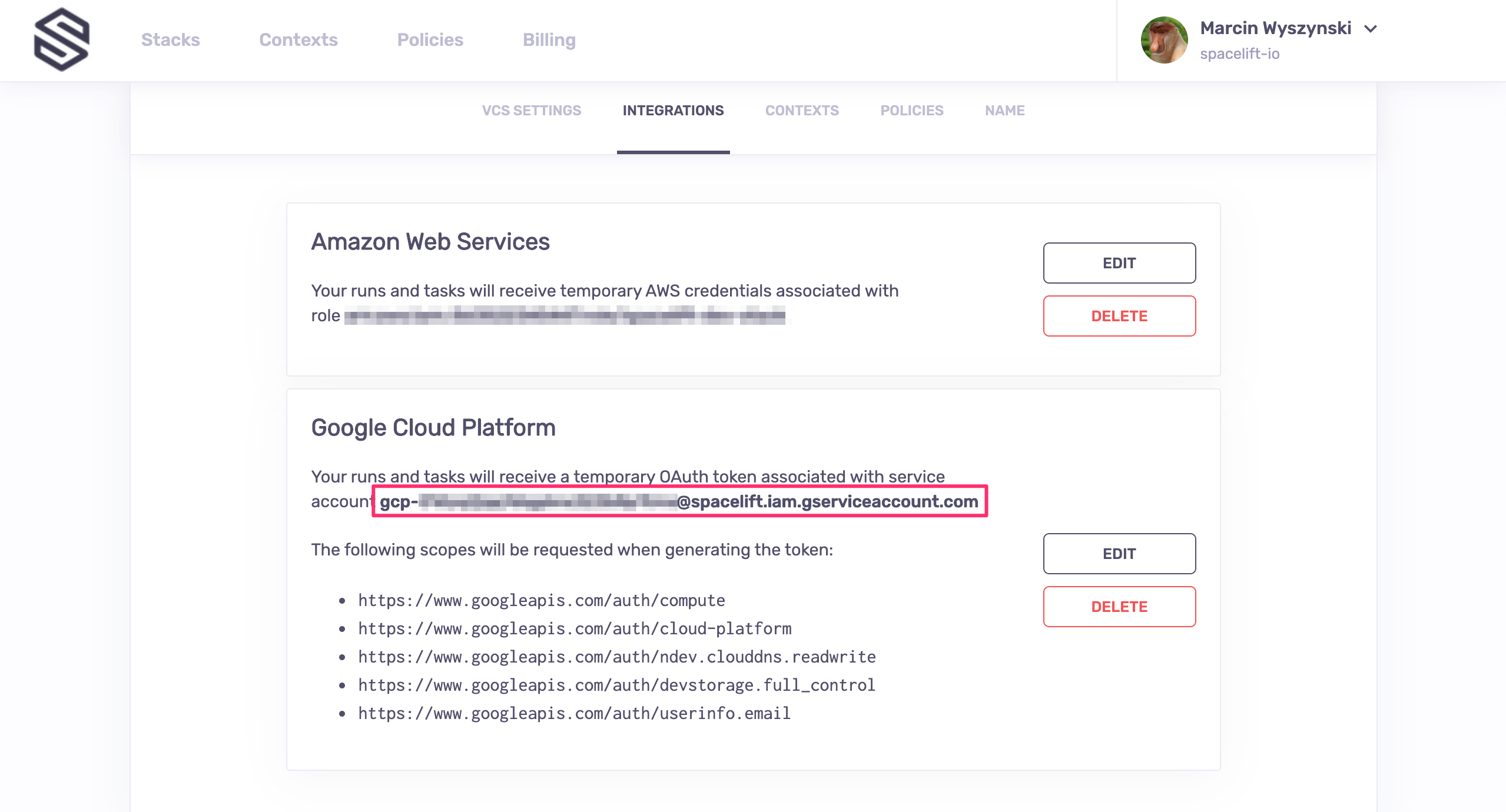
Once the integration is attached, Spacelift will display its globally unique service account email. You will use this email to set up access in GCP.
Set up programmaticaly in Terraform»
If you're using Spacelift Terraform provider to create the integration programmatically, you can do the following to configure the GCP integration and OAuth scopes:
1 2 3 4 5 6 7 8 9 10 11 | |
If the service account linked to your stack has sufficient privileges on the GCP organization, you can programmatically create a dedicated GCP project and set up the integration from the Google side of things:
1 2 3 4 5 6 7 8 9 10 11 | |
Set up access in GCP»
To make the integration work, you need to make the dedicated service account a member of your organization and/or project, with an appropriate level of access. This is done in the IAM & Admin view of GCP's web UI.
Organization level»
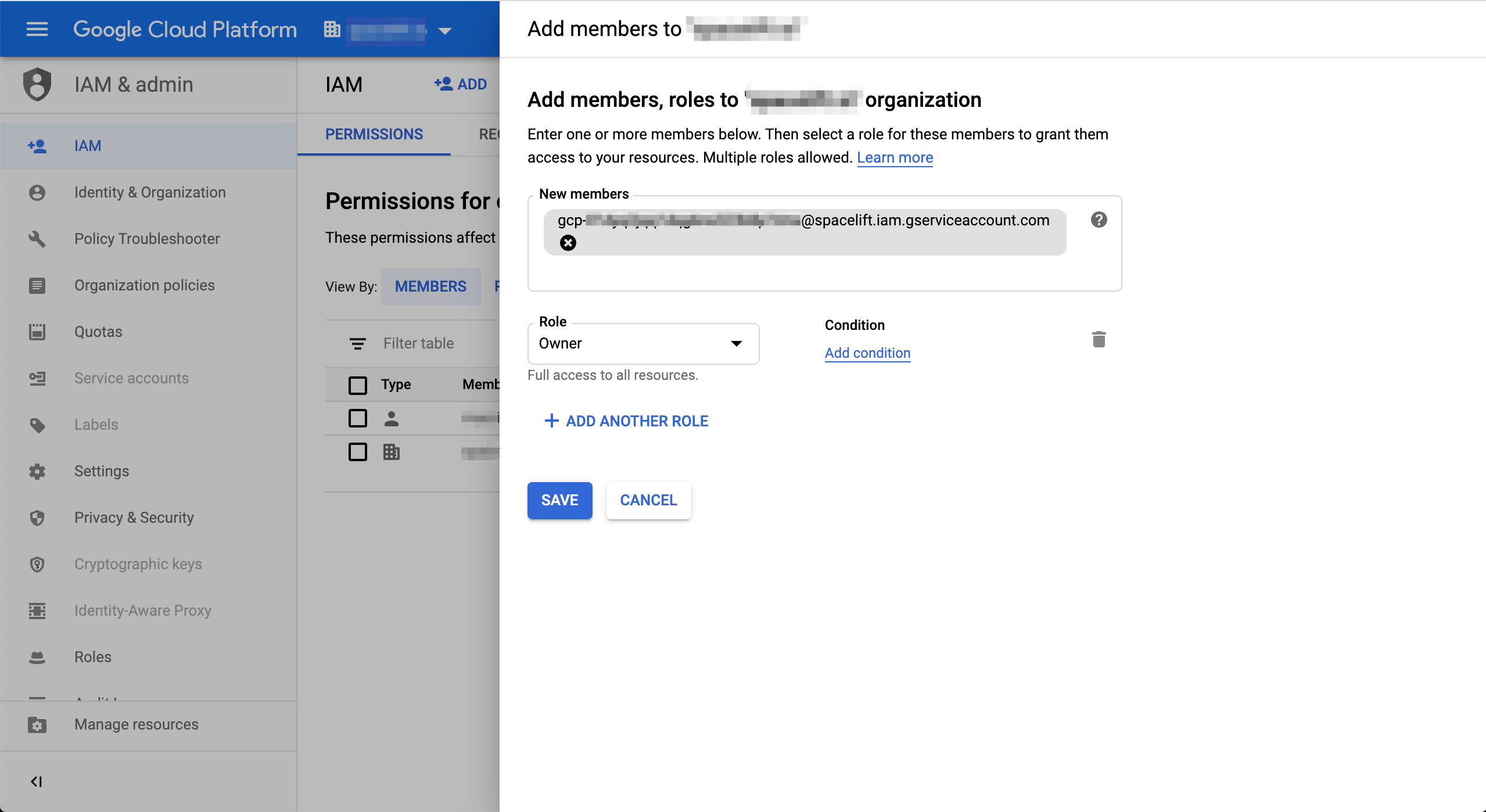
This is what you should see when adding a service account as a member on the organization level:
Info
In the above example, we made the service account an owner of the organization, giving it full access to all resources. Depending on your use case, you may want to alter the permissions.
Project level»
The process of adding a service account as a member on the project level looks absolutely identical except that projects are represented by a different icon in the dropdown:
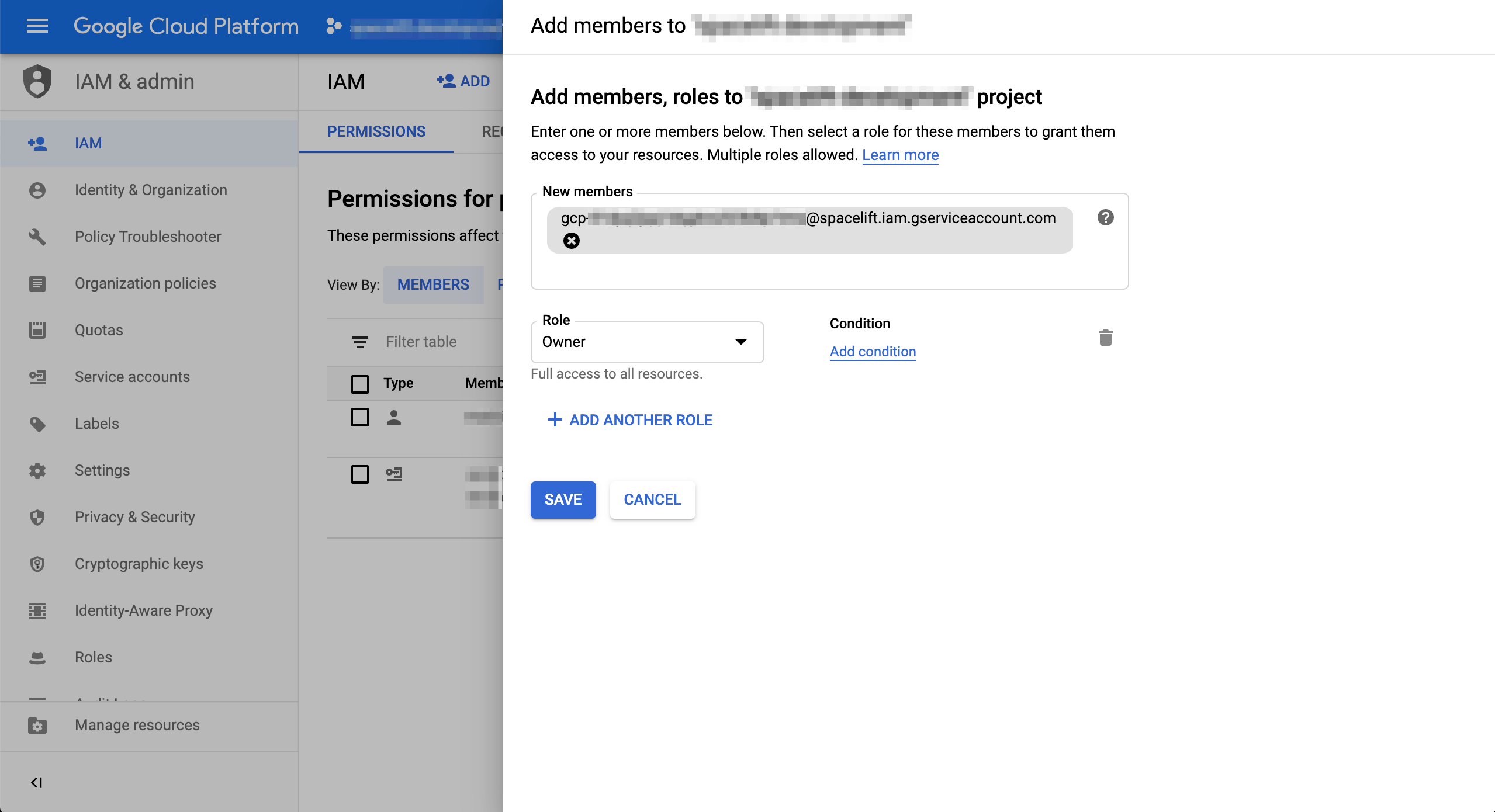
It can take up to a minute for the membership data to propagate but once it does, your Spacelift-GCP integration should be active.