Integrate Spacelift with Microsoft Azure»
Spacelift provides support for managing Azure resources via the Terraform Azure Provider. The documentation for the Azure Provider outlines the different authentication methods it supports, and it should always be considered the ultimate source of truth.
This page explains how to configure the Spacelift-managed integration, the simplest way to get Azure up and running as your cloud provider in Spacelift. The Spacelift-managed integration handles automatic secret creation and rotation.
Other authentication methods
See our Azure cloud provider documentation to set up the integration through static credentials or managed service identities.
Set up the Microsoft Azure cloud integration»
Tip
This guide explains how to configure the Azure provider using environment variables. Although you can add these environment variables directly to individual stacks, it may be worth creating a Spacelift context to store your Azure credentials. This allows you to easily add the same credentials to any stack that requires them.
The Spacelift-managed integration is great when you want to get up and running quickly, and when you want to ensure the credentials for accessing your Azure account will be automatically rotated and stored securely. If you are not comfortable with Spacelift managing your Azure credentials, we would suggest that you use a private worker configured with a managed identity for the most control and security.
Credential storage and rotation»
When an Azure integration is created, an associated Microsoft Entra Application is created within Azure. We automatically create a client secret for that application, and rotate it roughly once every 24 hours. The secret is stored securely, encrypted using AWS Key Management Service.
Step 1: Find your Active Directory Tenant ID»
Before creating the Spacelift Azure integration, you need your Tenant ID.
- Within your Azure portal, navigate to either:
- The Azure Active Directory section of the Azure portal.
- The Subscriptions section of the Azure portal.
- Locate and copy your Tenant ID.
Step 2: Create the cloud integration in Spacelift»
-
On the Integrate Services > Discover all integrations screen, click View on the Azure card, then Set up integration.
-
Fill in the integration details:
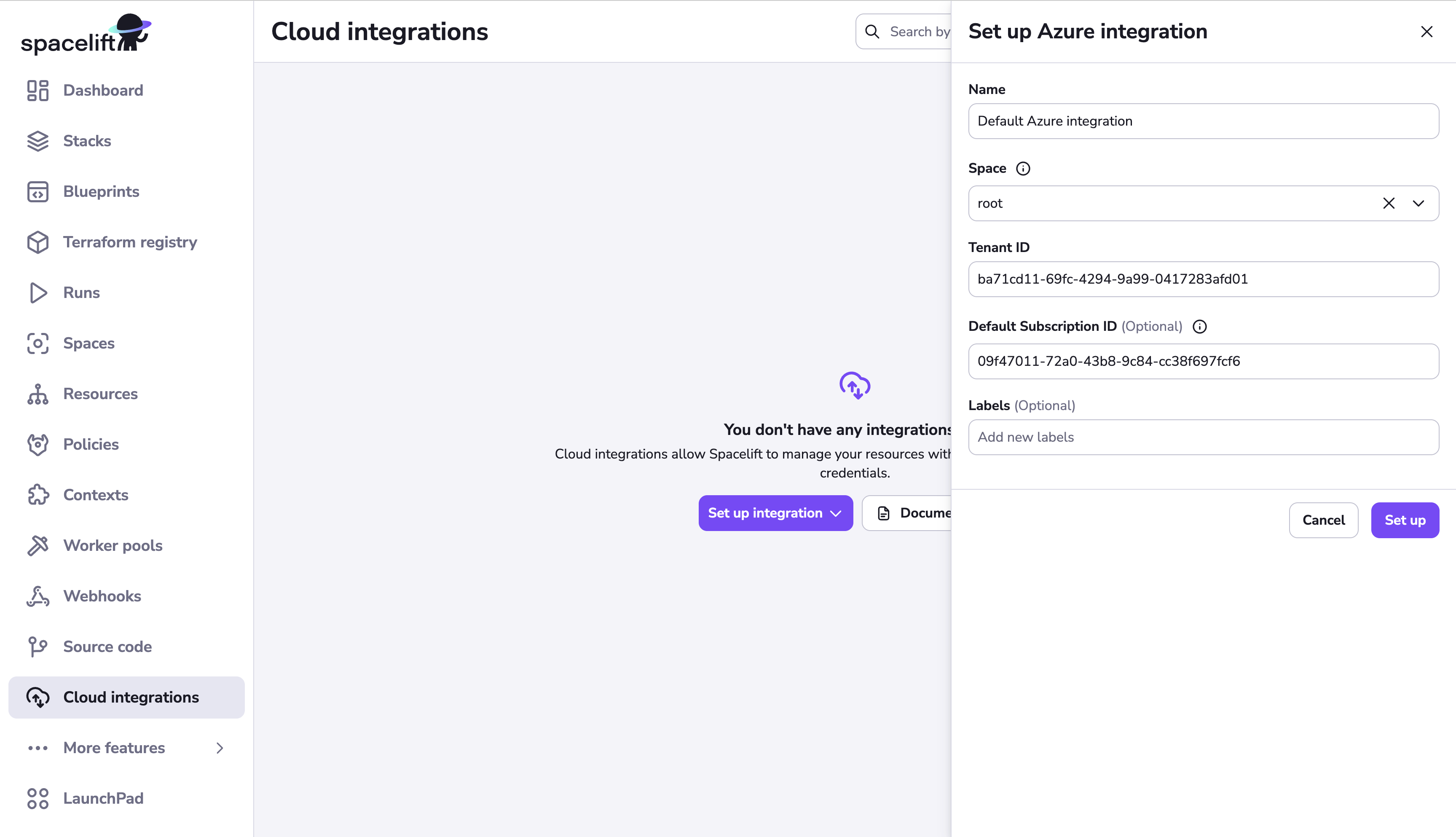
- Name: Enter a name for the cloud integration.
- Space: Select the space that can access the integration.
- Tenant ID: Paste the Tenant ID copied from the Azure portal.
- Default subscription ID (optional): If you want to attach your Azure cloud integration to multiple stacks all using the same Azure subscription, specify a default subscription ID here. This field is required if you want to use auto-attach.
- Labels (optional): Enter a label or labels to help sort your integrations if needed.
- Enable auto-attach (optional): If enabled, the integration will be automatically attached to any stacks or modules that have a matching label. To use this feature, add a label with the format
autoattach:<your_label>to the integration, then enable this toggle. Any stack or module with the<your_label>label will have this integration auto-attached.
- Click Set up.
Step 3: Provide admin consent»
Once your integration has been created successfully, you will be taken to the integration details page to provide the required admin consent. The consent process requires Spacelift to request at least one permission. Although Spacelift requests the “Sign in and read user profile” permission, it never signs in as any users in your account or accesses their information.
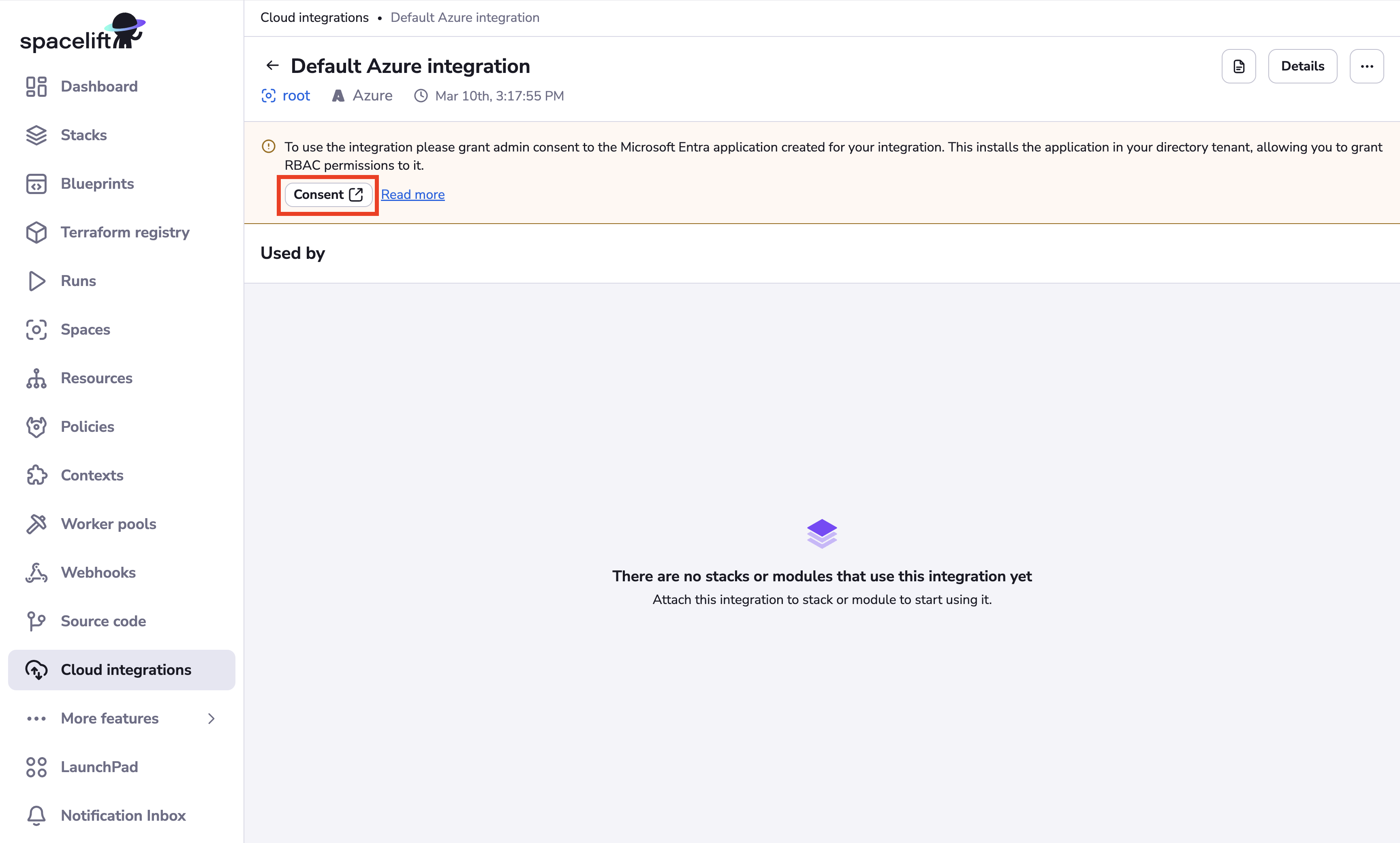
- Click Consent to install the Microsoft Entra application for your Spacelift integration into your Azure account.
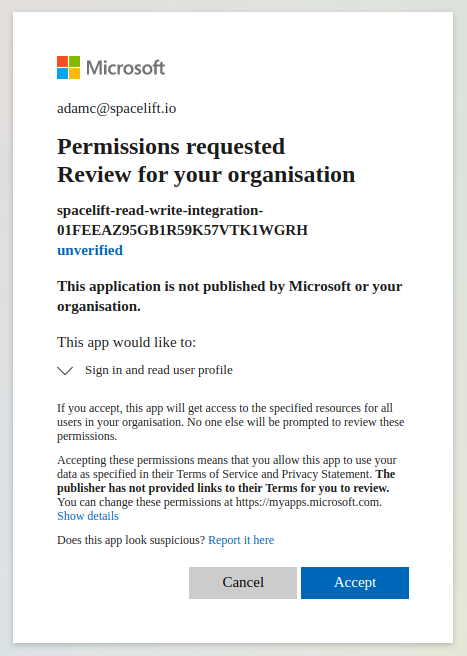
- Log in to your Azure account, if needed.
- Click Accept on the permissions screen to complete the admin consent process.
- You will be redirected back to Spacelift's Azure integration settings.
Possible error message
Microsoft Entra uses eventual consistency to replicate new Azure applications globally. Because of this, you might see the following error message if you try to grant admin consent too quickly after the integration is created:
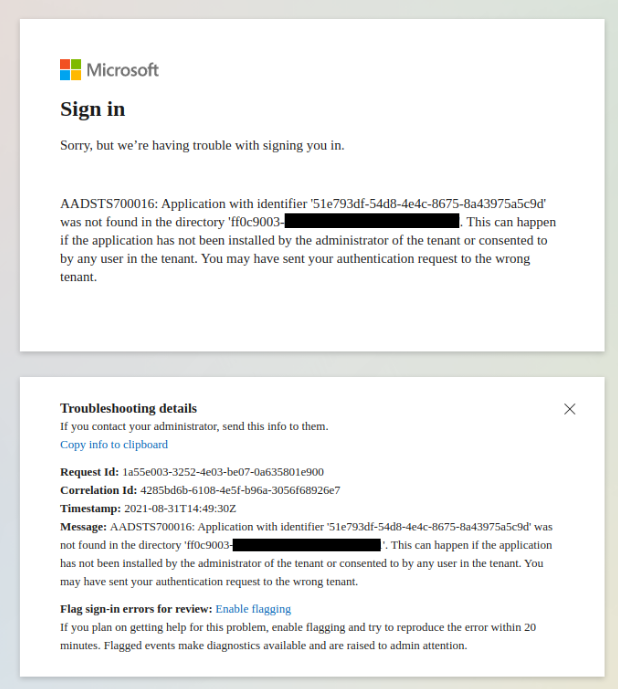
This isn’t a problem. Just wait a few minutes and try again.
Step 4: Configure Azure permissions»
Now that you have granted admin consent, a new Enterprise Application will be created for your integration in the Enterprise Applications section of Azure Active Directory.
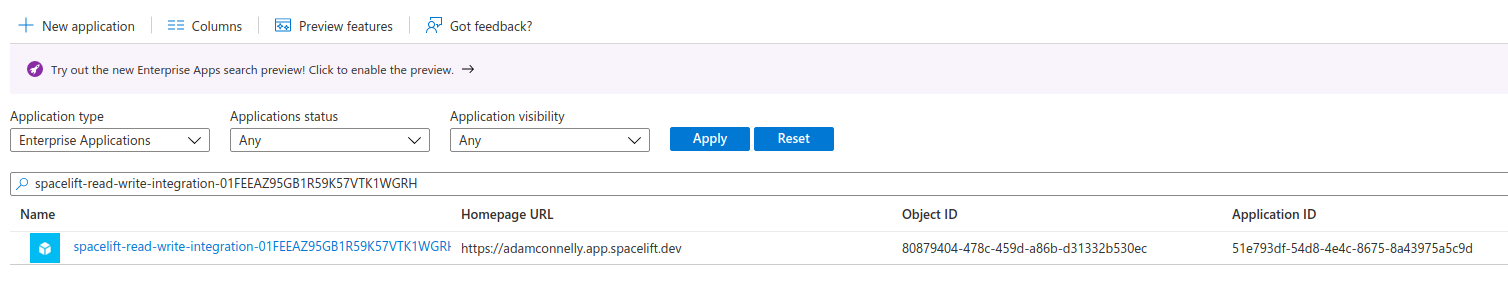
You will need to add a new role assignment for the Spacelift integration.
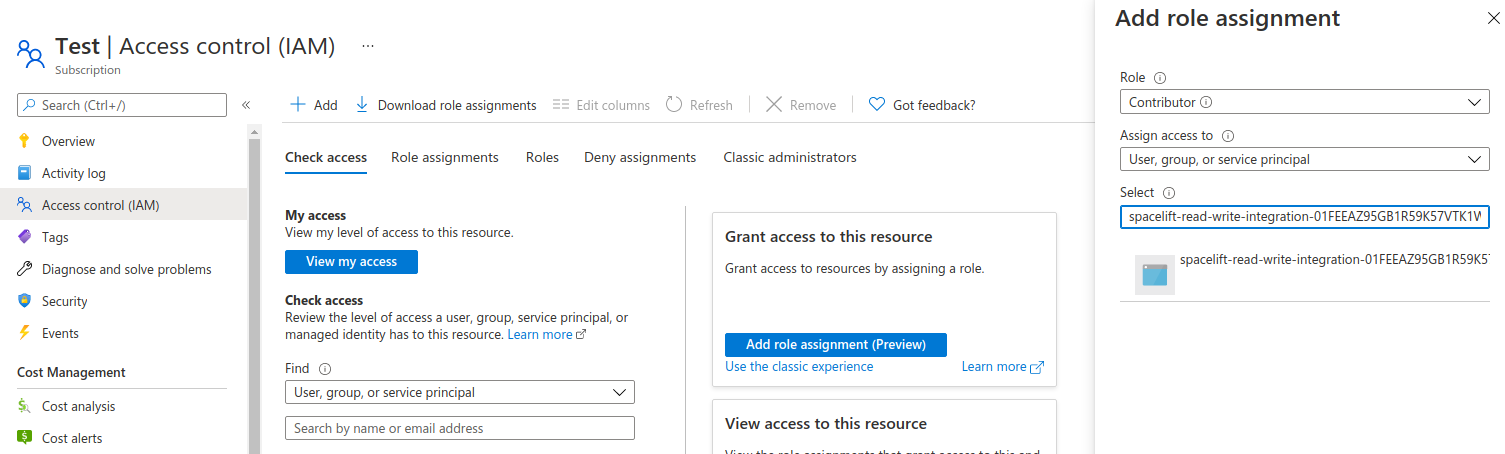
- Navigate to the Access Control (IAM) section of the Azure subscription or resource group you're integrating with Spacelift.
- Click Add > Add role assignment.
- Role: Select Contributor.
- Assign access to: Select User, group, or service principal.
- Select: Select the Spacelift Enterprise Application name from the list.
- Click Review + assign.
Info
The Spacelift integration has no access to any of your Azure infrastructure unless you explicitly grant it the appropriate permissions.
✅ Step 2 of the LaunchPad is complete! Now you can create your first stack.